On Securing What Truly Matters

Russia’s invasion of Ukraine and the preceding series of destructive cyberattacks have left many questioning what they can do to secure themselves in times of geopoltical unrest. This article proposes a four-step hands-on approach to cyber resilience: Identify, Secure, Monitor, and Plan. The central argument is that before effective security measures can be taken, organizations must first identify their critical assets and internet-facing attack surfaces. Only then can they take the necessary steps to secure themselves in an effective, risk-based way.
It's all about survival
Thanks to thousands of years of evolution, the human body has developed complex systems to protect us from danger. In the digital world, we don't have these natural defenses. To protect crucial digital technologies during crises, we need to outpace evolution. We can do this by applying survival strategies from the physical world to the digital one.
Lesson number one is that we must first familiarize not just with the enemy, but also with ourselves (our critical digital infrastructure and internet-facing attack surface). This lesson of introspection as a path towards security can be traced all the way back to 500 BC where Chinese military strategist Sun Tzu famously stated that “if you know the enemy and know yourself, you need not fear the result of a hundred battles”. Luckily, thanks to for example CrowdStrike's brilliant Global Threat Landscape report, we already know very much about the enemy. And since we know many of the enemy’s tactics, there will be more to gain if we focus on identifying our critical digital infrastructure and our attack surface.
Lesson number two is that once we have mapped out these critical systems they must be patched, secured, and hardened. Again, there is no need to reinvent the wheel. Experts in cybersecurity advisory such as CISA, NCSC, DoD and Mandiant have published (and continue to publish) excellent guides and tutorials that explain how popular digital systems can be secured. These will be explicitly referenced throughout the article.
Lesson number three is that we must establish visibility of our surroundings, in this case our critical digital infrastructure and digital attack surface. Just like shops use CCTV cameras to spot thieves and investigate robberies, organizations should use logging and Endpoint Detection and Response (EDR) tools to detect, mitigate, and recover from cyberattacks.
Lesson number four is that we have to train as we fight. Resilience is the capacity to recover quickly from difficulties; to bounce back. In the context of defensive cybersecurity, resilience is the ability to both withstand and recover from cyberattacks and other information security incidents. As with all other skills, the best way to improve on this ability is through rigorous planning (for example through scenario analyses and development of emergency procedures) and training (for example by practicing data recover processes and by performing perimeter security tests and red team exercises).
Building digital resilience: Applying the four survival strategies to critical infrastructure and attack surface
Now that we understand the strategies that keep us alive in the physical world –identifying our weaknesses so we can secure them, monitoring our surrounding, and training as we fight – we can begin to apply them to our digital infrastructure. Think of each individual phase in this four-step approach as a supporting brick in a game of Jenga. Remove one and the entire tower – your organization's entire security posture – collapses.
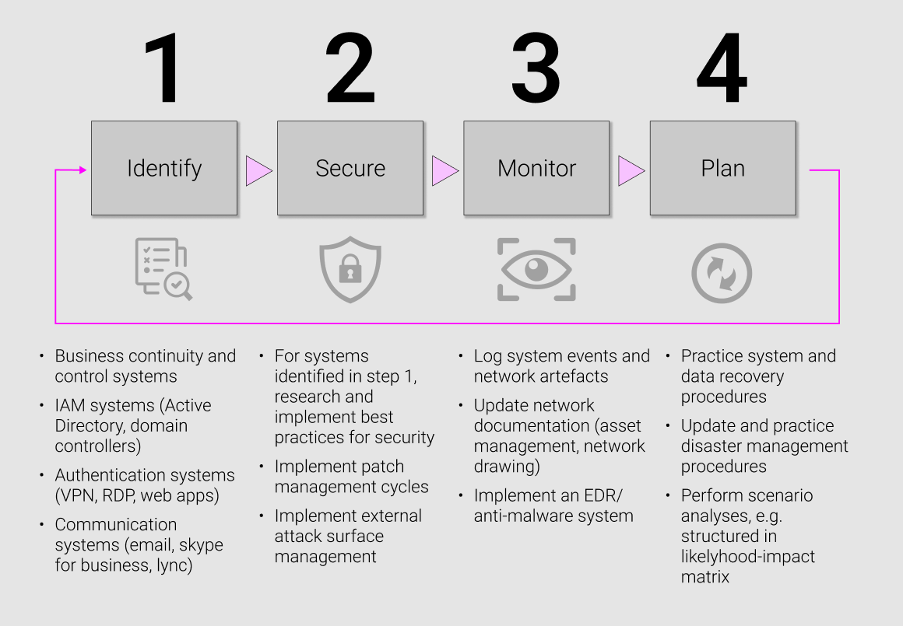
Identify
First, critical digital systems must be identified. Critical systems are assets (whether physical or virtual) that are so vital to your organization that their incapacitation or destruction would have a debilitating effect. There is no definitive list of what constitutes a critical system; this will vary tremendously from industry to industry. Without cranes and radio systems, a harbour would not be functional. Without their email and corporate VPN systems, a big multinational consultancy would not be able to operate.
In both times of peace and crisis, keeping an accurate and updated inventory of digital assets is key. The logic behind this is very simple: It's not possible to protect assets which you don't know exist.
One general way of keeping a structured overview of assets in a corporate network is through a network diagram. A network diagram is a visual representation of the relations between physical and logical systems and devices that communicate over the network and/or relay network traffic, such as firewalls, routers, switches, printers, and workstations. Network diagrams visualize network segmentation, individual servers' IP-addresses, and remote systems such as Cloud solutions and (B2B) VPNs.
Resource A: How to make a network diagram
While a universally applicable list of critical systems cannot be made, it is possible to make a widely generalizable list of common attack vectors, that adversaries target to gain initial foothold in the vast majority of cases. Securing these vectors of attack are almost as important as creating and maintaining a list of critical digital assets, which brings us to the next step in the process of attaining cyber resilience in times of crisis: Security and hardening the identified critical systems and commonly exploited attack surface.

Secure
Second, the identified critical systems and common attack vectors must be secured and patched. Many critical systems are not exposed to the open internet and will therefore not be reachable to attackers who scan your organization for vulnerabilities and vectors of attack. Examples of such systems are PLCs, SCADA environments, and other industrial control systems. The most widely used and implemented digital technologies, however, are both exposed to the open internet and critical at the same time.
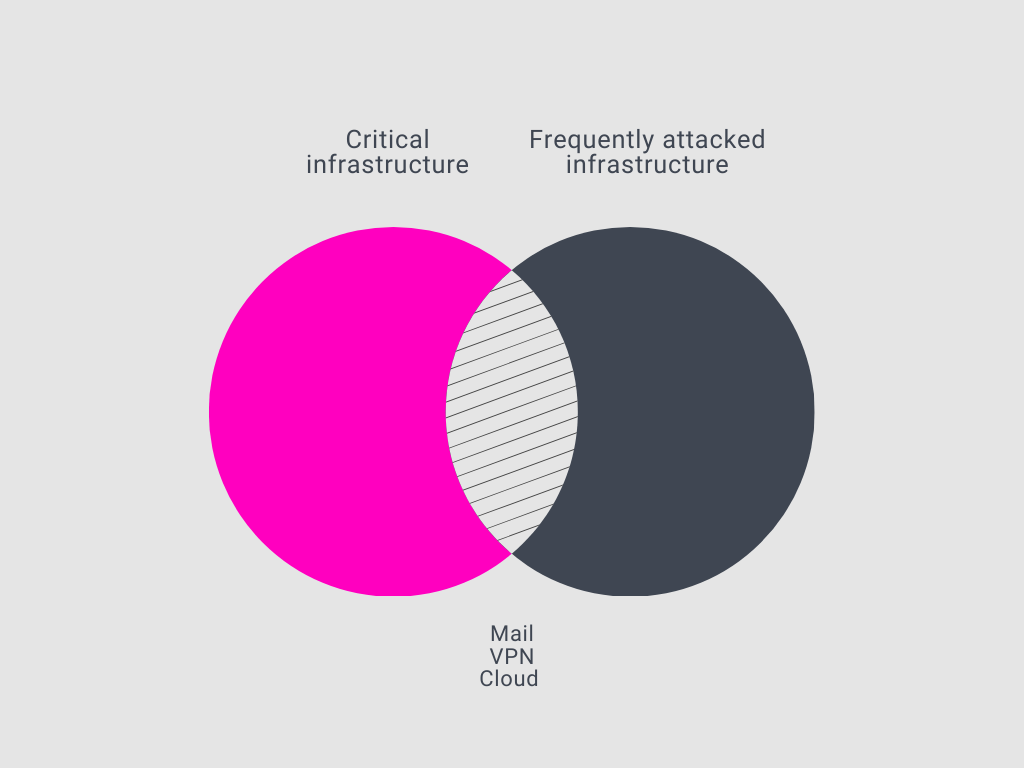
Some of the most frequently attacked digital systems that often also will be deemed critical are:
- E-mail systems such as on-premise Microsoft Exchange or Microsoft O365
- Web applications exposed to the open internet that validate against Active Directories
- Corporate VPNs such as Cisco AnyConnect or Citrix GateWay
- Cloud storage systems such as Amazon S3 or Azure Blob
- Cloud containers and virtual machines such as Amazon EC2 or Azure VM
Not only do these systems account for almost all initial compromises; they are also so deeply embedded in the organizations who use them that it would have a debilitating effect if they were compromised. These systems should therefore be prioritized over all others in the process of securing and hardening.
Luckily, experts in the field of cybersecurity such as CISA, Microsoft, Mandiant and Cisco have published (and continue to publish) outstanding advisories for securing them.
Resource B: Microsoft's guide to O365 hardening
Resource C: NSA's guide to securing VPNs
Resource D: CISA's guide to securing Cloud
Monitor
Third, the identified critical and frequently attacked systems must be monitored closely and continuously to detect, prevent, and respond timely to security incidents. A common misconception is that logging can be achieved by setting a checkmark in the software's management interface. While this is not entirely false, the base configuration of most ‘out of the box’ network and event logging omits many of the most vital artefacts necessary for forensic experts to determine the scope and origin of a compromise. A common example of this are web servers that do not by default keep the external IP-address of the originating system (X-Forwarded-For) in their access log. Another example is firewall logs that only log certain protocols, fail to specify the number of bytes in a session, or fail to specify session lengths.
Ideally, visibility should be established through (centralized) logging of host- and network-events. This can be accomplished with a Security Information and Event Management (SIEM) system which collects network logs from switches and firewalls; access logs from web applications such as VPN, mail, and cloud; audit and security logs from Domain Controller(s); and logs from hosts with deployed and configured Endpoint Detection and Response (EDR) systems. Regardless of the type of logging, the quality of the monitoring will be determined by the degree of visibility, the knowledge and insight of the monitored network, and the granularity of the logged details.
Resource E: OWASP's cheat sheet to logging
Plan
Fourth and finally, emergency and business continuity management plans must be developed and, importantly, rehearsed. As with all other skills, defensive cybersecurity expertise can only be attained through rigorous practice. The best way to practice cyber emergency procedures is to train as we fight train. So ask yourself the following questions:
- Are we able to recover systems and data from offline backups?
- Where can these backups be found and who is responsible for the recovery process?
- How can we protect ourselves from DDoS attacks and other causes of sudden spikes in traffic?
- Who can we contact if we need urgent Incident Response?
- How can we maintain communication with key actors if the mail system doesn’t work?
Resource F: Mandiant's guide to proactive preparation and hardening
Resource G: Belfercenter's Cybersecurity Campaign Playbook
Conclusion
With the aim of helping organizations defend themselves in times of crisis, the article has proposed a four-step framework for cyber resilience. The framework argues that a cycle of identifying, securing, and monitoring critical systems and common vectors of attack can ensure survival and business continuity, but only if emergency planning and training is institutionalized.
If you liked this article or found it useful, please sign up to webscout and join the waitlist through the form at the bottom of our landing page to be notified of new powerful features. Thank you for reading. Stay safe!
About the author
Jonathan A. (@deadsyn_), founder of webscout.io.

