How to secure your e-mail and prevent most cyberattacks

Accounting for upwards of 90% of all cyberattacks, email continues to be the most frequently exploited system. Given the availability of technologies that can improve the security of mail systems, and given the ease with which mail servers can be managed, it is embarrassing that even fortune 500 companies continue to get caught with their pants down. This blog post seeks to make it crystal clear what you should and should not do to significantly strengthen your mail security. It identifies three steps through which this can be achieved: Know yourself, know your enemy, and apply this knowledge pro-actively.
Learning email security from the Art of War
Emails are every modern organization's biggest vulnerability. From malware to malware-less attacks including impersonation attacks like CEO fraud, a single malicious email can cause significant brand damage and financial losses. Understanding this ever-evolving threat is necessary to stay ahead of attackers, and we want to argue that part of the key to reaching this understanding can be found in Sun Tzy's theory of war:
"If you know your enemy and yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained you will also suffer a defeat. If you know neither the enemy nor yourself, you will succumb in every battle." Sun Tzu, The Art of War
This seminal quote is as true for cyber security as it was for kinetic warfare in 5th century BC China, and it speaks for itself: To succeed in battle, you must know the enemy, you must know yourself and you must apply this knowledge in a rational, pro-active way. The following section informs you about each of these three crucial steps so you can master the art of (cyber) war from a defensive perspective.
Step 1: Know yourself
It goes without saying that self awareness is a key value in all aspects of life, but when it comes to securing digital infrastructure, keeping a cool and collected overview of systems can be a daunting task even for small organizations. To make this task more digestable it can be broken down into two seperate (but complimenting) processes: An internal process and an external process.

Know your systems from within: Asset management
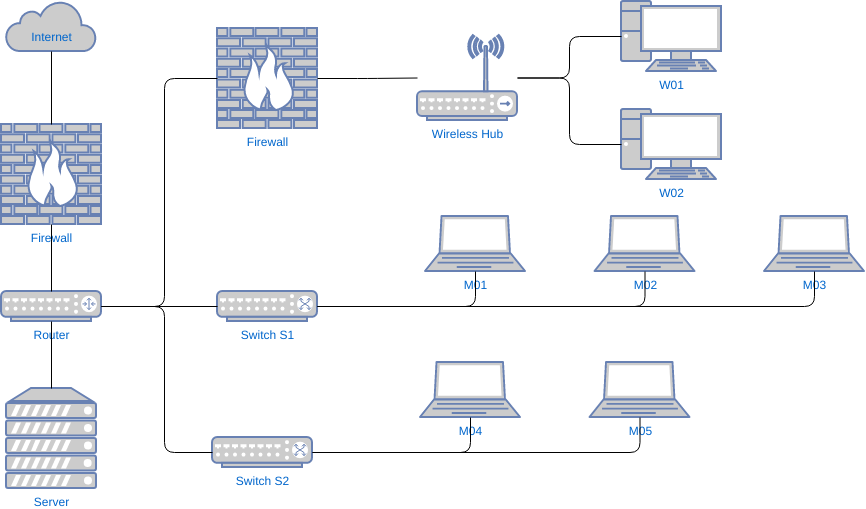
IT asset management (also known as ITAM) is the process of ensuring that an organization’s IT assets - hardware, software, networks, websites, cloud services, mobile devices etc. - are accounted for. Put simply, it’s making sure that the valuable items of technology - tangible and intangible - are documented. Keeping an updated inventory of digital assets is key to tracking, securing, and ensuring that it is used effectively. There are many suppliers of IT asset management solutions, but good asset management does not have to cost thousands of dollars. From a security perspective, simply keeping an updated network diagram of servers, switches, network segments, firewalls and IP-addresses can prove invaluable. If your organization does not currently have an overview of the network, we urge you initiate the production of one as soon as possible. In case of an attack and a potential compromise, a well-documented network diagram can mean the difference between life and death for your organization.
Know your systems from the outside: (External) attack surface management
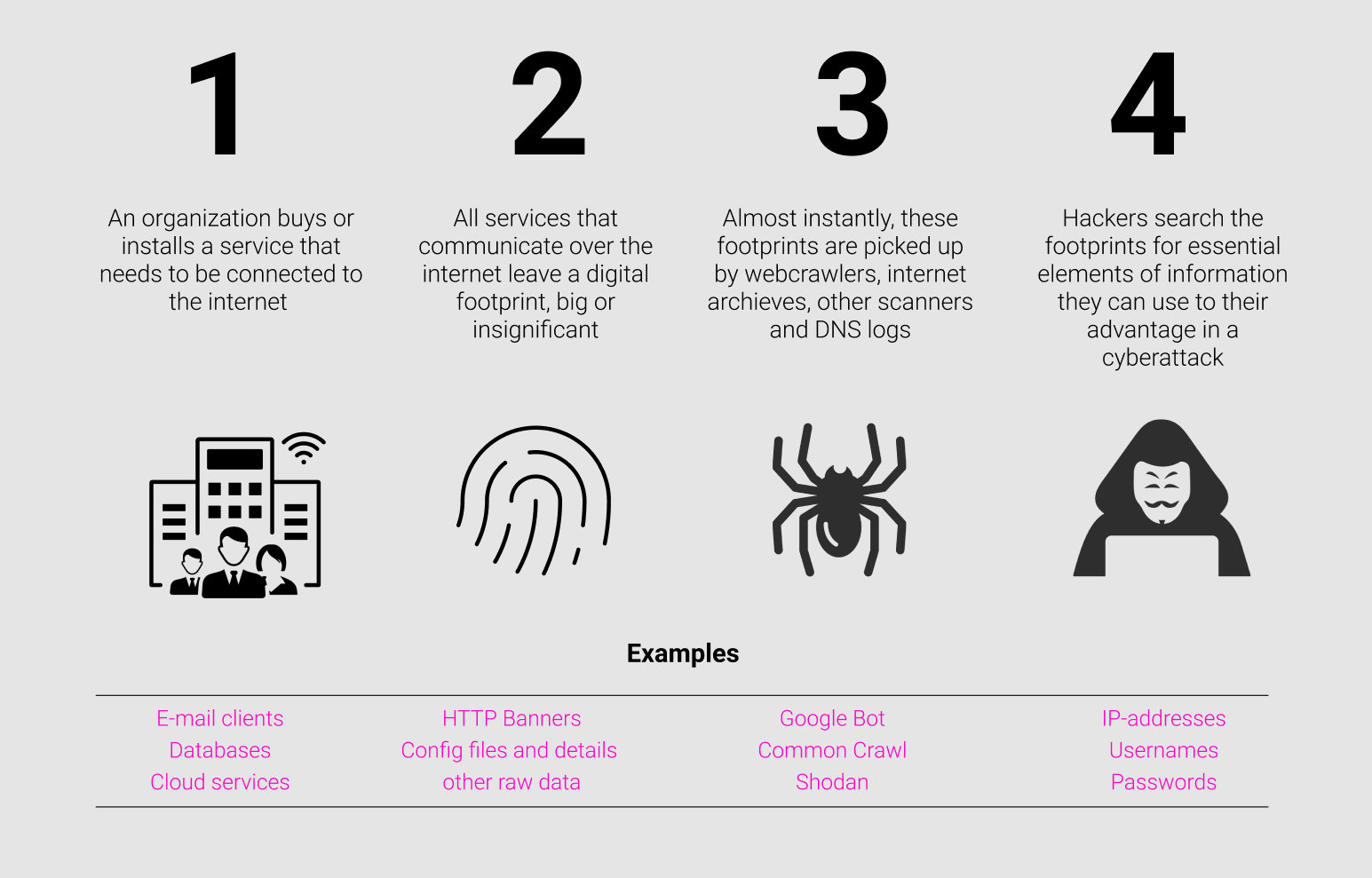
Attack Surface Management is about effectively managing all the vulnerabilities that exist as a result of an organization’s online presence. Management is the process of dealing with things or people. In the context of Attack Surface Management, these “things” are vulnerabilities. Attack Surface Management guides leaders, managers and security professionals through the steps an organization should take to secure its digital attack surface. In other words, Attack Surface Management wants to make it as easy as possible for organizations to minimize the risks associated with them being connected to the internet. In the context of Attack Surface Management, “vulnerability” is a broad term that refers to every piece of information available on the internet that hackers, cyber criminals, ransomware gangs and other malicious cyber actors can abuse to gain unauthorized access to your organization. In that sense, vulnerabilities are not just limited to a specific CVE, an insecure server, an open firewall etc. Examples of vulnerabilities in scope for Attack Surface Management are leaked e-mail addresses, usernames, passwords, login pages, phone numbers, open databases, company secrets, domain registrar information, open ports, and of course also all the traditional vulnerabilities mentioned before.The concept of online presence is important for Attack Surface Management because it stresses that every interaction with the internet leaves a small digital footprint. The concept of online presence is naturally closely interlinked with the concept of vulnerability: Seemingly harmless interactions with the internet produce artefacts that all hackers, from amateurs to highly skilled and organized groups, can abuse. The image below illustrates how everyday organizational processes give rise to digital vulnerabilities that cyber adversaries are constantly looking to exploit.
Step 2: Know your enemy - mail based phishing attacks
Now that you know yourself, the second step towards securing your mail is to become familiar with the digital enemies in cyberspace and the tactics, techniques and procedures (TTPs) they deploy to compromise your systems thorugh phishing. Phishing attacks are by far the most common - but also most effective - type cyberattack. In phishing attacks, hackers attempt to lure victims into doing 'the wrong thing', such as clicking a bad link that will download malware, or direct them to a dodgy website that will steal their credentials or perform other malicious actions. Phishing emails can reach millions of users directly, and hide amongst the huge number of benign emails that busy users receive. Phishing emails hit all types of organizations every minute of every hour, 365 days a year. There are six 'give aways' to a phishing email thay you sould know:
- Urgent call to action or threats
- First time or infrequent senders
- Spelling and bad grammar
- Generic greetings
- Mismatched email domains
- Mismatched email domains
Urgent call to action or threats. Be suspicious of emails that claim you must click, call, or open an attachment immediately. Often they'll claim you have to act now to claim a reward or avoid a penalty. Creating a false sense of urgency is a common trick of phishing attacks and scams.
First time or infrequent senders. While it's not unusual to receive an email from someone for the first time, especially if they are outside your organization, this can be a sign of phishing. When you get an email from somebody you don't recognize, or that Outlook identifies as a new sender, take a moment to examine it extra carefully before you proceed.
Spelling and bad grammar. Professional companies or organizations usually have an editorial staff to ensure customers get high-quality, professional content. If an email message has obvious spelling or grammatical errors, it might be a scam. These errors are sometimes the result of awkward translation from a foreign language, and sometimes they're deliberate in an attempt to evade filters that try to block these attacks.
Generic greetings. An organization that works with you should know your name and these days it's easy to personalize an email. If the email starts with a generic "Dear sir or madam" that's a warning sign that it might not really be your bank or shopping site.
Suspicious links or unexpected attachments. If you suspect that an email message is a scam, don't open any links or attachments that you see. Instead, hover your mouse over, but don't click, the link to see if the address matches the link that was typed in the message. In the following example, resting the mouse on the link reveals the real web address in the box with the yellow background. Note that the string of IP address numbers looks nothing like the company's web address.
Mismatched email domains. If the email claims to be from a reputable company, like Microsoft or your bank, but the email is being sent from another email domain like Yahoo.com, or microsoftsupport.ru it's probably a scam. Also be watchful for very subtle misspellings of the legitimate domain name. Like micros0ft.com where the second "o" has been replaced by a 0, or rnicrosoft.com, where the "m" has been replaced by an "r" and a "n". These are common tricks of scammers.
Step 3: Pro-actively apply what you know about yourself and what you know about your enemy

Now that you know yourself and your enemy, you can begin to take action by applying the things you have learned to proactively secure your mail systems. Once you have checked everything in the list below, congratulations! Your mail is now more secure than over 90 percent of the mail systems out there.
- Manage exposed e-mail addresses and usernames
- Implement multi-factor authentication for both users and admins
- Enable unified audit logging
- Enable preset security policies in Exchange online
- Enable external email tagging
- Disable macros across your domain groups or enforce that all documents are opened in sandboxed environments
Manage exposed e-mail addresses. First, go through all the exposed emails identified by Webscout's domain harvester. Do this with the following question in mind: Should this e-mail address really be accessible to everyone with an internet connection? If the answer is 'no', then the account should be terminated and the employee in question should be assigned a new e-mail address. Naturally, it can be in an organization's strategic interest to have some addresses exposed to the public. We do this too (info@webscout.io) so we can answer your questions. However, most company email addresses should never be exposed to the internet; especially not together with their passwords. Weeding out exposed e-mail addresses is the most crucial step in your email attack surface management.
Implement multi-factor authentication (MFA) for both users and admins. Enabling multi-factor authentication (MFA) is the most recommended security measure to secure a mail solution. It protects accounts against phishing attacks, password spray attackers and many other classes of cyberattack. Importantly, multi-factor authentication should be enabled for all admins and user accounts; no exceptions. If possible, MFA should not just be enabled on mail systems; it should be enabled on all your organization's internet-facing authentication systems. The effectiveness of MFA cannot be overstated. Implemented correctly, MFA continually proves to be an extremely effective security measure.
Enable unified audit logging. It goes without saying that you should do everything to prevent unauthorized access and to your mail, such as implementing MFA and disabling inactive users, but it is equally important to plan ahead in case someone manages to compromise your systems anyway. Logging allows you to trace back how an attack happened and which actions the hacker took against your systems. This is very important: Both to assess the damage, to effectively remediate and to ensure that the hacker is kicked out of your environment. In Office365, mailbox audit log is enabled by default, but the Unified Audit Log should also be enabled for a much more detailed view of potentially malicious actions. Each entry in the Unified Audit Log is kept for 90 days by default, but you should increase this retention time if possible.
Enable preset security policies in Exchange online. Microsoft has created two preset security policies for Exchange Online, a standard policy and a strict policy which both automatically implement securitu policies to protect your Exchange Online environment against the latest attack trends. The advantage of this is that you don't need to have an in-depth understanding of advanced security policies; all this is handled by Microsoft's experts with this 'click and run' solution that automatically updates your settings with Microsoft’s latest security recommendations. You can find the policies in Window's Security and Compliance Center.
Enable external email tagging. A newly released feature in Exchange Online allows you to tag external emails. This feature is very useful because it makes it very clear where an email comes from. Hackers will often 'spoof' internal e-mail addresses to make it seem like an email sent from the hacker is sent from within the victim organization. For example, hackers will mimick your service desk accout (servicedesk@yourdomain.com) by sending phishing emails from servicedesk@gmail.com which any unaware user would fall for. By automatically tagging all external emails, we can make it more clear for the users that the email was sent from outside the organization.
Disable macros and open documents in sandboxed-mode. The best defence against phishing mails with malicious attachments (sometimes referred to as malspam) is to disable macros. This can be done either locally on host machines or through Group Policy management in Microsoft's Trust Center.
While these are some of the most effective things you can do to secure your mail here and now, there are many other ways to strenghten you security. Check out Microsoft's excellent blog post on the topic.

Thank you for reading. Stay safe!
About the author
Jonathan A. (@deadsyn_), founder of webscout.io.

