How to make a Network Diagram and why every organisation should

An updated diagram showing how an organization’s network is structured is an incredibly important yet often neglected piece of documentation. Every organization that takes its digital security seriously should have one. This blogpost presents a guide on how to make one and explains the benefits of each important step along the way.
When it comes to detecting or recovering from a cyberattack, the presence of a good map of the network can mean the difference between spending a fraction of the security budget on Incident Response, or exceeding it greatly. Only with an updated network diagram can responders to a cyberattack structure their analysis and begin to theorize about the attackers’ paths through the network. Without one, responders must work slowly in the dark. This blogpost is split into two major sections. The first section explains what a network diagram is, and the second section presents a practical guide on how to make one.
What is a network diagram?
In a robbery of a physical bank, investigators can follow some very tangible leads. It is not hard to tell how the robbers broke into the bank if there is a car inside of the office and a giant hole in the wall. Similarly, fingerprints can be collected from the counter and CCTV footage can be replayed to find out who did what, where and when.
In the digital world, the investigative clues are much less tangible. We can’t just look at a physical server rack and determine which systems that were compromised. And we can’t just dust the network switch for fingerprints to find out who the hackers were. Due to the elusive nature of cyberattacks, to answer the same investigative questions that we ask in real-life crime scenarios, we must take a deep-dive into the network, and it all begins with a network diagram.
A network diagram is a visual representation of the nodes in a network. Nodes are physical and logical systems and devices that communicate over the network and/or relay network traffic. Common examples of such nodes are firewalls, routers, switches, printers, and workstations. Network diagrams connect these nodes with a line (an “edge”) to visualize connectivity, device relationships or network topology/hierarchy.
Example one: The good network diagram
What is a good network diagram? Unfortunately, there is no be-all end-all tutorial to building a good network diagram. Networks vary tremendously in size and complexity so it would not be productive to define specific rules for network diagram creation. That being said, there are some general properties that are considered to be universally good when it comes to network diagram design:
- A good network diagram is intuitive to read
- A good network diagram clearly depicts network topology and device connectivity
- A good network diagram shows external systems that connect to the internal network
- A good network diagram holds (references to) information about IP-addresses, hosts, and segments
A high-quality network diagram strikes the balance between visual clarity and technical detail. One (simplified) take on a such a diagram is depicted below. Note that the fourth property concerning IP-addresses has been left out for simplicity.
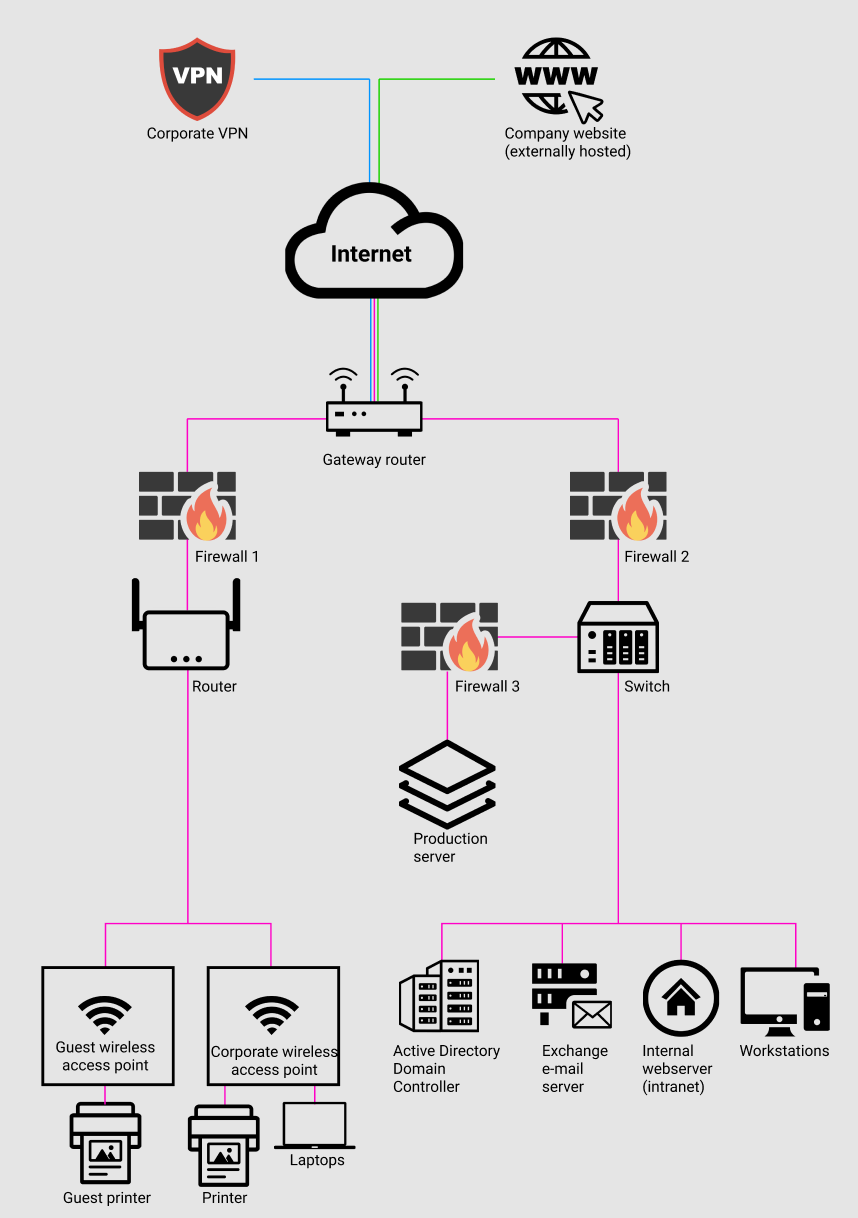
The diagram above clearly shows the structure of the example organization’s network. It shows how the network is segmented between Wi-Fi and workstations and it is intuitive to understand roughly how traffic flows from one device to another. Additionally, it shows there are two external assets outside the local network: A corporate VPN and a webserver hosted remotely by a third party. All this information comes in handy during an investigation of a cyberattack regardless of its severity.
One important element that has been left out in the example diagram above are the network’s collection points. Collection points are the nodes in the network (physical as well as virtual) that log important data and events. For example, a firewall should log network sessions (a “firewall log”) and a web server should log interactions with a website (a “web access log”). The reason why depicting collection points is so important is because it allows for responders to quickly survey the network and secure the necessary logs that will form the basis of the investigation. I have omitted collection points from the example diagram to keep the blogpost more focused, but I plan to dedicate an entire blogpost to the topic.
Example two: The bad network diagram

A bad network diagram, generally, is one that does not adhere to the four properties described above: One that isn’t intuitive to read; doesn’t clearly depict device relations; doesn’t visualize external assets; and fails to include relevant information about hosts and IP-addresses.
There are many ways to make a bad network diagram, but even the most obscure and unintuitive network diagram is better than nothing: The worst network diagram is an empty one. Even the most generic information about a network can be invaluable for investigators in the case of a cyberattack. Without a network diagram, investigators must slowly pave their way through the network in darkness.
During an Incident Response, there are several questions that forensic investigators wish to answer:
- How did the attackers get in? (Vector of attack)
- How did the attackers traverse the network? (Paths of lateral movement)
- Which systems and data might the attackers have had access to during their unwelcomed stay? (Damage assessment)
- What are the paths of exfiltration? (Damage assessment)
If no network diagram exists, and if the victim has little or no logs from affected systems, it will not be possible to answer these key forensic questions. Other than rolling out Endpoint Detection Response (EDR) systems and establishing network monitoring “post mortem”, there is not a lot that can be done. If this is the case, sometimes the worst-case scenario must be assumed: That a full domain compromise has taken place, every organization’s worst nightmare.
How to make a network diagram
Now let’s turn to the second and final section of this blogpost: How to create a good network diagram. The steps presented here apply best to small and medium-sized organizations, but even organizations with highly complex networks should benefit from the guide.
Creating a network diagram does not have to cost tens of thousands of dollars, and it does not need to include external consultants or network security architects. In many cases, the diagram can be made and maintained by single system administrator, but it obviously depends on the size and complexity of the network. With attack surface management and risk minimization in mind, this section breaks down the process of creating a network diagram into four consecutive steps.
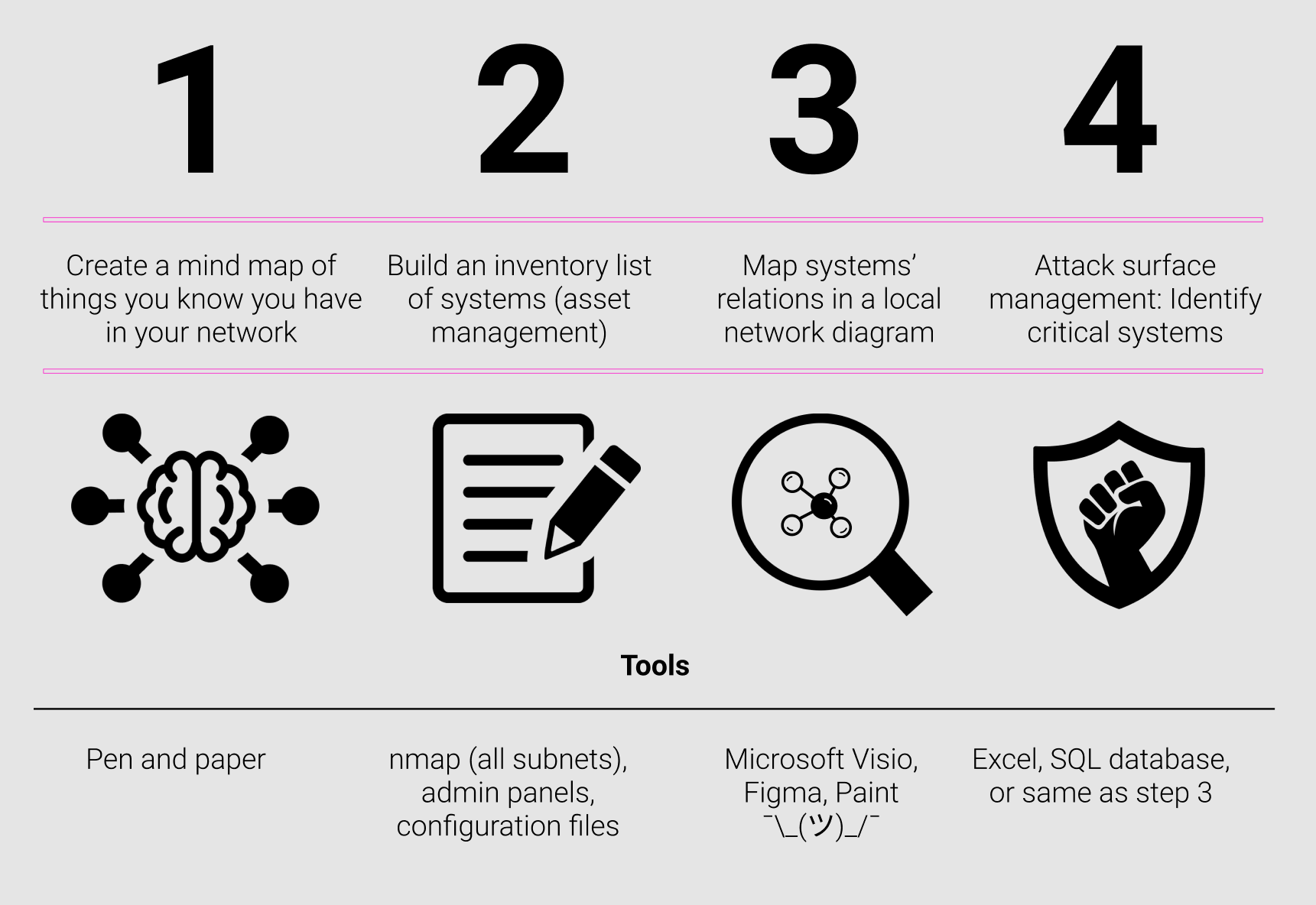
1. Creating the mind map
The first step in the process of creating a network diagram is to create a mind map of all the systems anddevices in your network that you can think of. No matter how familiar you are with your network, you will have some general knowledge of its topology, even if you think that you don’t. For example, you will know your organization’s website; if it has one or more printers; if it has a wifi access point; and what kind of email solution it relies on. Maybe you are also aware of firewalls, switches, and servers. Regardless how deep your knowledge of your network is, the best way to start the network diagram creation process is to map what you know and use this as the starting point for the next steps.
2. Building the inventory list
The next step is to fill all the gaps in the mind map you made in step one, and it is by far the most involved and time demanding step of them all. In this step you will have to describe all systems, physical and virtual, in your network: Their IP-addresses, operating systems, and their general purpose. A threefold approach to this is proposed: Start from the top, map hubs and relays, and go down stream.
Start from the top. Your gateway router is arguable the most important piece of equipment in your entire network. It is the item that connects your organizations internal network (“intranet”) to the open internet (“extranet”). All inbound and outbound connections go through this router, so it is a natural first item to add to your inventory list. When you add it to the diagram, it is important to document both its public and its private IP-address. Its public IP-address is what the gateway looks like from the outside when connections are made from the extranet, for example 221.10.32.20, and its private IP-address is what the gateway looks like when it communicated with devices within the organization, for example 10.10.10.1 or 192.168.10.1. Documenting both the internal and the external IP-address should be done for all systems that are open to the internet.
Map hubs/bridges/relays such as firewalls, switches and routers. Once you have added your gateway router to the network diagram, you can move on to the next step: Locating the network devices that relay, parse and inspect network traffic. It is common for even relatively simple networks to have at least one child router or switch that act as a hub between the network’s nodes (such as workstations, printers and servers) and the gateway router, such as the example network from section 1 in this blogpost. Additionally, networks have firewalls that filters out unwanted traffic. Firewalls can be both virtual (such as web application firewalls) and physical (many are familiar with CISCO boxes). Firewalls play a vital role in the network, so it is important to add them to the inventory list.
Move down river. The final things that should be added to the inventory list are all the endpoint systems whose traffic pass through the network devices described in the section above. Such endpoint systems include (but are not limited to) client computers, mail servers, databases, VLANs, WIFI networks, (industrial) control systems, Domain Controllers, etc. From a security perspective, the reason why it is so important to map this layer of the network is because this is where a lot of the ‘good stuff’ can be found: E-mails, blueprints, trade secrets, images, videos, databases, and so on. In other words, it is this part of the network that most adversaries will seek to reach through the various firewalls, switches and routers between the clients and the edge router / internet gateway.
3. Mapping system relations
The third step involves making the actual visual representation of the network where nodes (systems and devices in the inventory list) are connected by lines (”edges”) which represent topology and how traffic flows in the network. In other words, this step is about projecting the inventory list onto a canvas where the network’s hierarchy and its relations are clearly depicted.
Microsoft’s Visio-software ships with an excellent module which makes it very easy to draw a detailed, professional-looking network diagram:
- Open Microsoft Visio
- Go to File > New
- In the search box, type Basic Network Diagram or Detailed Network Diagram
- Drag the shapes you need to draw your network onto the drawing page from the Computers and Monitors and Network and Peripherals stencils.
- Arrange them into an order that makes it clear where the network origin and end points are, and how the various nodes are linked.
- Add connections to show how devices are linked. Use AutoConnect for basic connections and the Comm-link shape for wireless connections.
- Revisit the inventory list and add labels and data to the devices depicted in the diagram (most importantly IP-addresses).
- To add a simple label simply click a shape and begin to type. To store data with a shape, click View > Task Panes > Shape Data. In the Shape Data window, type the IP address, network name, and other data that you want to store.
- Alternatively, if you have Visio Professional, you can simply import the inventory list to automatically assign labels to the shapes you have in your diagram. On the Data tab in Visio, click Quick Import and browse to the location of the inventory list.
Microsoft has made a great video tutorial on these steps which can be found here. Additionally, they have published a written tutorial which can be found here.
4. Manage the attack surface
The fourth and final step views the information stored in the network diagram through the eyes of attack surface management, thus transforming a static diagram into an active tool for cyber defense.
First, go through each node depicted in the diagram and ask you’re the following questions: How bad would it hurt if this system got compromised by a hacker? How likely is it? A tool to aid this process is a simple likelihood-impact matrix:
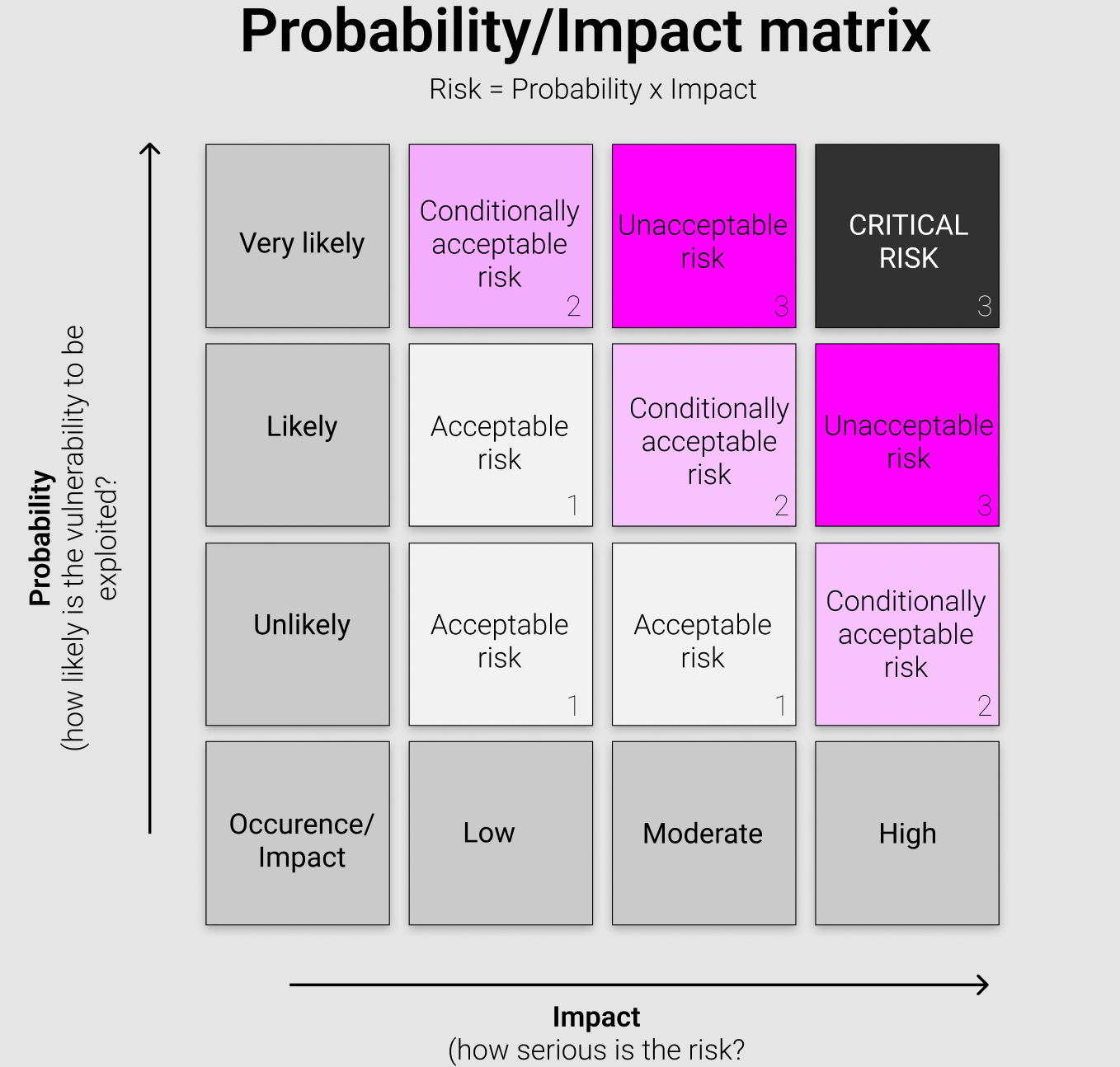
Viewing the network diagram through the lens of attack surface management should make it clear where in the network the ‘crown jewels’ reside; which systems are critical and which are not. This knowledge can then feed directly into pro-active cyber defense of the most essential systems.
Second, go through each node which is exposed to the open internet (the ‘extranet’) and enumerate which endpoints they have exposed; how they authenticate to other systems on the intranet; and which technology stacks they are built on. Additionally, ask if you keep patch management of each system. If you do not, then set the process in motion immediately. If you do, ask when they were last updated and check if there are any known CVEs (exploit-db.com) associated with their respective patch levels. This second step has been covered in much more detail in the blogpost “Understanding Attack Surface Management, cyber security's next ‘big thing’” [link xx].
Final thoughts
Before rounding off, it should be noted that network diagrams are beneficial for many other purposes than simply security. Other organizational units that can benefit greatly from a well-kept network diagram are the system admins, service desks, and financial units. For sysadmins they are useful when network-related issues, such as congestion and packet loss, need to be effectively identified and fixed. For service desks they are useful when managing the Active Directory, and for financial units they help mitigate shadow IT which is a growing problem for most modern organizations.
The point is that network diagrams should not only live in the system administrator’s drawer. They should be viewed as (and integrated into) the organization’s larger IT Asset Management program. IT asset management (also known as ITAM) is the process of ensuring that an organization’s IT assets - hardware, software, networks, websites, cloud services, mobile devices etc. - are accounted for. Put simply, it’s making sure that the valuable items of technology - tangible and intangible - are documented. Keeping an updated inventory of digital assets is key to tracking, securing, and ensuring that it is used effectively. There are many suppliers of IT asset management solutions, but good asset management does not have to cost thousands of dollars.
Finally, network diagrams should be treated as highly sensitive, confidential documents. In the hands of an attacker, they will guide them directly to the most valuable digital possessions.
Thank you for reading. Stay safe!
About the author
Jonathan A. (@deadsyn_), founder of webscout.io.

